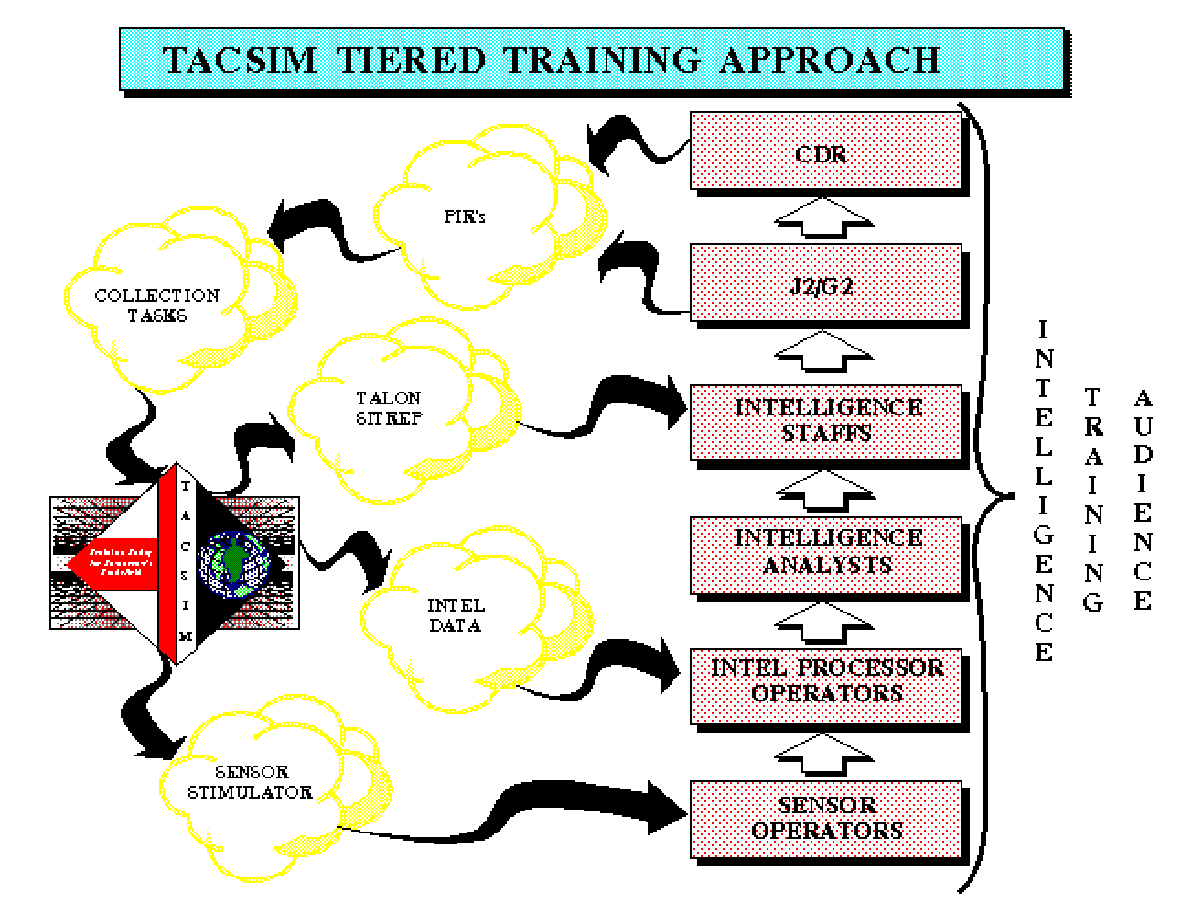
Figure 1. TACSIM Training Approach
1995 Southeastern Simulation Conference
Roger D. Smith
Mystech Associates, Inc.
Manassas, Virginia 22110
Military officers are trained at exercises such as "Reforger", "Team Spirit", "Ulchi Focus Lens", and "Central Fortress". Which use a mixture of live and simulated equipment. The Military Intelligence (MI) component of this training audience uses the events to improve their abilities to locate, identify, and evaluate the intentions of the enemy forces. The Tactical Intelligence Simulation (TACSIM) replicates the operations of intelligence collection platforms, sensors, and data pre-processors.
At some exercises it is not possible to deliver the TACSIM produced reports to the intelligence analysts. This may be due to several reasons: 1) the analysts are not present at the exercise, 2) the analysts are not located in a facility that is cleared to receive the intelligence reports, or 3) the analysts are members of an allied nation which is not allowed to receive the raw data directly. To accommodate all of these situations, the simulation is equipped with the TACSIM Analysis Operations Node (TALON), a military intelligence semi-automated forces system (MI-SAF). This accepts the reports, and with the help of information about the training scenario, attempts to replicate the operations carried out by the intelligence analysts. A summary report is produced which is appropriate for delivery directly to the intelligence officers, and is at a lower classification level that can be released to a broader audience.
This paper describes the techniques and operations of TALON. The system architecture and algorithms used to fuse intelligence reports and produce inferences about the identity of the enemy are explored. The fusion engine performs the basic functions: feature analysis, record correlation, data fusion, and data degradation. The paper details some of the applications to which the system has been put in addition to its primary analysis mission. Limitations of its capabilities are explained and plans for enhancing its ability to replicate human operations described. Future TALON development could form a foundation for exploring simulation-based system design.
INTELLIGENCE TRAINING EXERCISES
Training exercises like "Reforger" and "Ulchi Focus Lens" are used to prepare U.S. soldiers to operate effectively during real combat situations. The exercises are a combination of live maneuvers using real equipment and simulated assets on networks of computers. By combining the two it is possible to take advantage of the realism of operating in the field and the safety of performing dangerous maneuvers in computer simulation. Simulations such as the Corps Battle Simulation (CBS), Air Warfare Simulation (AWSIM), and Tactical Intelligence Simulation (TACSIM) are networked together and share a common view of the battlefield through the use of a shared protocol. Each is designed to stress a particular component of the military command structure. In this paper we will discuss one of the systems created to aid in the training of the military intelligence (MI) component by providing a semi-automated force to perform intelligence analysis and fusion, an MI-SAF.
MI officers are part of a staff referred to as the G2, which serves intelligence to the battle commander. It is their job to collect information on the activities of the enemy and to asses their future intentions. This information is then used to guide the operational planning cycle. These officers receive their picture of the battlefield from a cell of intelligence analysts. That cell pours over hundreds or thousands of intelligence reports in order to piece together a single integrated picture of the enemy forces. In the real-world the reports received are generated by yet another layer of pre-processors that are responsible for converting electronic signals and photographs into textual reports. In a simulation exercise the signal/image collection and pre-processing are performed by the TACSIM system. It generates reports in the official message format and at rates which match that of the real-world sensors. Since the reports are correctly formatted they can be delivered via standard military communications systems such as AUTODIN and TRAP Broadcast. They can also be processed by real-world intelligence workstations: the All Source Analysis System (ASAS), Phoenix, Warrior, Enhanced Tactical Users Terminal (ETUT), and the Electronic Processing and Dissemination System (EPDS). These connections to operational command post equipment increase the realism of the training situation for the analysts and improve the effectiveness of the training.
FUSION REQUIREMENT
TACSIM is designed to force both the intelligence analysts and staff officers to perform their tasks as they would during an actual conflict (figure 1). This requires that TACSIM generate a huge number of reports, on the order of thousands per day. Handling this volume of message traffic is a full-time job for a dozen analysts. In the intelligence area this also requires the use of highly classified information and simulation models.

Figure 1. TACSIM Training Approach
The above two characterisitcs have typically been driving factors in determining the type of command structure that can be trained by TACSIM. However, in 1992, the Reforger exercise required that intelligence officers from NATO countries be stimulated by reports generated from the TACSIM system. This required the construction of a simulated intelligence data fusion system, the TACSIM Analysis Operations Node (TALON), to receive the message traffic that would normally be sent to an analysis cell. It fuses this data to produce a summarized output which describes the cogent information from the original reports. The summaries are delivered directly to the intelligence officers serving the G2 and contain only information at a very common classification level.
SYSTEM ARCHITECTURE
Though there is a wide scope to the intelligence training process (as indicated by figure 1), this paper will describe only the fusion engine and the report writer in detail.
A brief overview of the entire TALON architecture (figure 2) is necessary before describing the operations of the fusion engine itself.

Figure 2. Architecture of the TACSIM Analysis Operation Node
Data Sources
No war begins with a complete lack of intelligence about the opposing forces. In the best of cases the opponents have been facing each other across a defined border for years, as in the former East-West Germany. Under these conditions the MI sections have compiled a great deal of information about the enemy long before hostilities begin. Desert Shield provided several months of both operational and intelligence preparation prior to Desert Storm. In the simulation we use the initial scenario description data to represent this starting picture of the enemy forces. This is supplemented with a library of parameters which describe the characteristics and capabilities of the intelligence cells being simulated by TALON.
Once an exercise begins, a stream of data which describes the true movement and attrition occurring on the battlefield, is provided to TALON. This includes the rate of time advancement and the addition of new assets to the battlefield. As sensors collect data, intelligence reports are generated by TACSIM and provided to TALON for analysis and fusion. These fall into a few specific categories with a different set of key data in each: imagery, electronic, and communication intelligence (IMINT, ELINT, and COMINT respectively).
Parsing and Storage
Each of these reports is parsed into its basic data components and stored in a relational database. This component and the storage system are based on the Army Warrior Intelligence Workstation which forms the foundation for the TALON system. Since Warrior is used by real analysis cells which perform many of the TALON functions manually, it was a natural decision to use these capabilities in automating that process. This alleviated the need to create a database system, graphic query interface, map display, data parsers, and communications capabilities. The TALON team focused on the development of the fusion engine, report writer, and modifications to existing Warrior capabilities.
Fusion Engine
The fusion engine accesses the data that has been stored in the RDBMS. It extracts the pertinent fields and compares new information to a "master list" which describes the complete assessment of the battlefield. The master list is upgraded or downgraded to match operations in a real analysis cell. New intelligence reports and ground truth data result in an improved understanding of enemy activity. Late arriving reports, the limitations of the simulated analysts, and the dispersion of the reports through time result in a degraded understanding. Therefore, the intelligence picture is constantly in flux from the beginning of the exercise to the end.
The key fields in the input reports and the associated fields in the output reports vary by report type and are shown in figure 3. Each data field contributes to the fused product as shown. More details on this process are given in the following section.

Figure 3. Input to Output Data Field Mapping
Report Generation
The reports generated by TALON are Situation Reports (SITREPs); Size, Activity, Location, Unit, Time, and Equipment Reports (SALUTEs); and performance statistics (STATS) (figure 4). SITREPs are generated based on a specified time period and are responsible for painting the lion's share of the picture. SALUTEs are used to report information that has been designated as a "High Priority Target". As soon as this information is received the officers should be alerted to the fact, not waiting for the end of the SITREP reporting period. The performance statistics describe the number and quality of reports TALON and the number and quality of reports generated. This provides some insight into the scope of the data that is being handled on their behalf and indicates where modifications are needed to the sensor collection plans.
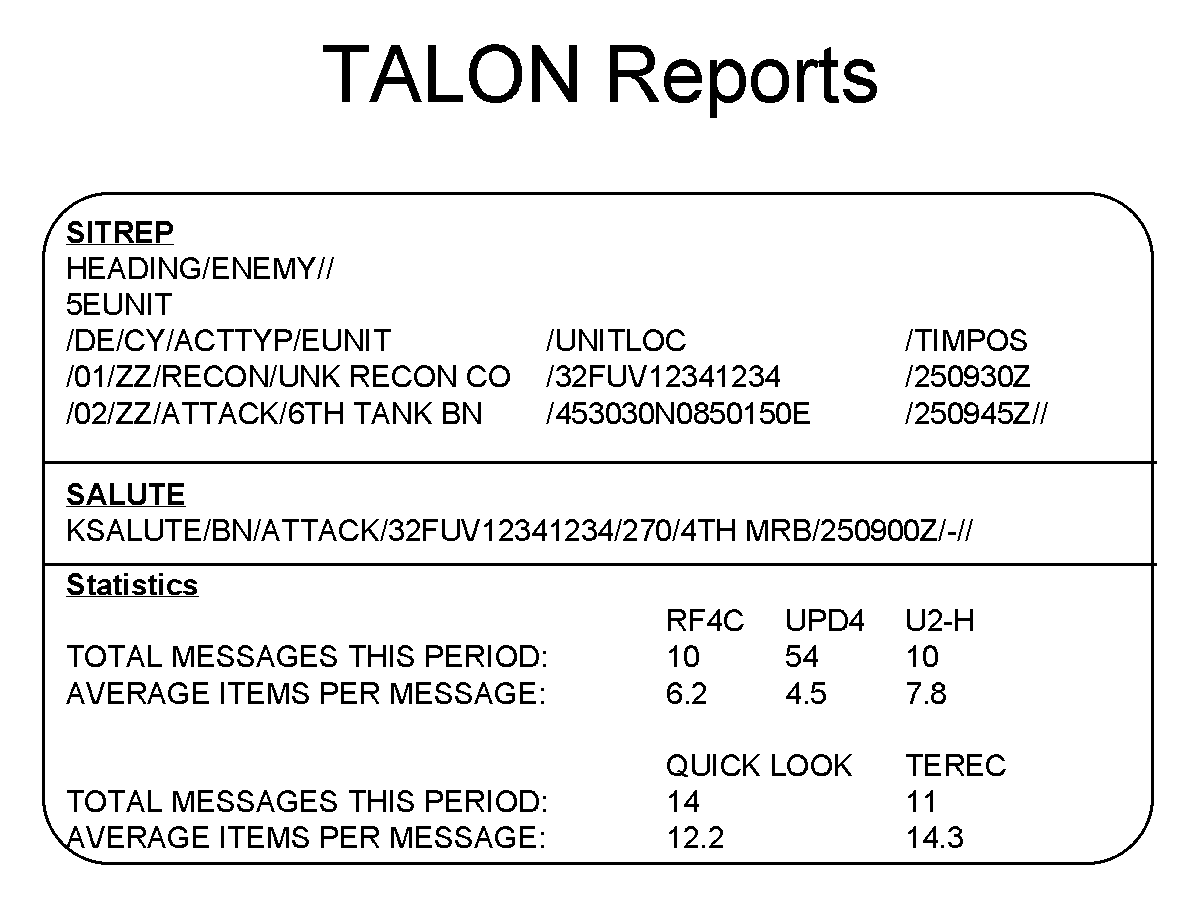
Figure 4. TALON Report Format Samples
Computer Hardware
TALON is designed to run on a Sun SPARC 2. It uses 64 megabytes of memory and 2 gigabytes of disk storage. The interface to the system is an X-Terminal which provides a windowed operating environment to the military operators. It is networked to the DEC VAX that is the host for the TACSIM system and the interface to the real-world communications network. TACSIM-TALON communications are accomplished via Remote Procedure Calls (RPC) and File Transfer Protocol (FTP).
FUSION METHODOLOGY
The heart of TALON is the fusion engine. This is responsible for transforming the detailed data available in thousands of IMINT, ELINT, and COMINT reports into a single coherent evaluation of the enemy forces. Figure 3 above described the pertinent fields in the raw reports and the goal data in the fused reports. Since TALON reports describe the enemy at command entity levels, the information generated includes the unit size, activity, location, type or name, time of detection, and list of equipment (the meat of a SALUTE or SITREP report). This is supplemented with a front line trace of the enemy force locations, the Forward Edge of the Battle Area (FEBA).
Feature Analysis
Within the raw reports key fields are identified for each intelligence discipline.
Imagery Intelligence. IMINT reports provide excellent location data on specific pieces of equipment. These are prime targets for location averaging to produce a single unit location. However, this discipline is a very poor provider of information about the activity and identification of the unit. But, special cases do exist, in which unique equipment can be identified to a level of resolution sufficient to identify a unit. The quality of the images may resolve an object as "Tracked Vehicle", "SAM Launcher", or "SA-2 Launcher". At the lower levels this provides little more than a count of the vehicles in the unit. At higher resolutions it can identify the type of the unit as a surface-to-air missile battery (as was seen by the general public in the U-2 pictures during the Cuban Missile Crisis). Special cases also exist for activity identification since it is possible to recognize certain formations from an image. Road movement by units deploying forward can be determined and river crossing activities are identifiable.
Unfortunately, images are one of the most time intensive forms of intelligence to collect. The reconnaissance aircraft must fly out to the site, take the photograph, and return to a base where the film can be processed and analyzed. This can take many hours, decaying the tactical value of the information. Synthetic aperture radar images can be produced on a more timely schedule. These are collected by aircraft operating closer to friendly locations and down-linking the data to processing centers in a form that is nearly finished.
Electronic Intelligence. ELINT reports provide medium quality data on location, activity, and identification. Electronic signatures indicate the type of radar emitter that is being used. This often implies the type of unit (such as a SAM unit) and may sometimes indicate a specific unit identification (such as an SA-2 Battery). This is accomplished based on the uniqueness of the radar signature within the family of radars being used on the battlefield. Those that are assigned to only specific types of units (SA-2, ZSU-4, etc.) can indicate exactly what assets are being detected. The historical database of intelligence on the area contributes greatly to this determination.
Unit locations can be determined by the sensors or by analysts working with several detections of the same emitter. The sensor identifies the direction from which the signal is coming. Technical parameters of the radar, such as its power output, can also be used to estimate the distance between the intelligence collector and the emitter. This provides an approximate location with a probabilistic error ellipse around it. This can be improved upon by triangulating several detections of the same radar from different collectors on the battlefield. This can greatly reduce, but not eliminate, the error ellipse.
Communications Intelligence. COMINT operates almost identically to ELINT, providing signature analysis and locations. Since radio signals are more refined that radar signals, this information can be determined to a greater degree. Given large data sets collected over time, it may even be able to identify the unit name and activity.
Record Correlation
Once features in a report have been analyzed, TALON performs cross-record correlation and fusion. The fusion engine maintains a master list of intelligence data. This is the equivalent of the old intelligence maps with pasted icons and descriptions written in grease pencil. As the information changes the icons are moved or replaced with ones that are more descriptive. The engine compares master list entries with new information coming in. The new information is used to improve the resolution of truth in the list. Data is processed using a value-drive method rather than a rule-based system. This environment defines relationships numerically rather than requiring a large number of rules to be created and related in order to track the data. All exercises are different to some degree, therefore, it would be difficult to construct a rule-base to cover all possible contingencies.
Correlation is the process of determining the relationships between new data and existing data in the master list. Many attempts to do this in intelligence correlation machines has resulted in algorithms in which the number of stored reports grows rapidly. This is due to the difficulty in determining which records are related. To side-step this problem TALON uses information about ground truth available from the simulation. This is the key differentiator between TALON and real-world fusion systems.
Data Fusion
Once correlated, records must be fused, a process with two basic objectives. The first is to derive unit information from the object information collected. The second is to integrate intelligence data through time so that the current fused picture represents information that evolves through time.
During the fusion process we are working on three primary characteristics of the enemy units: location, identification, and activity.
Location. Determining the location of a unit on the battlefield is not as straight-forward as it may at first appear. Though each object has a definite location, the unit itself is a conceptual entity made up of all of the objects. Its location may be considered the average of the locations of its equipment, the most densely populated area it controls, or the location of the command vehicle. This information also changes over time as the unit moves across the battlefield and changes its operational posture.
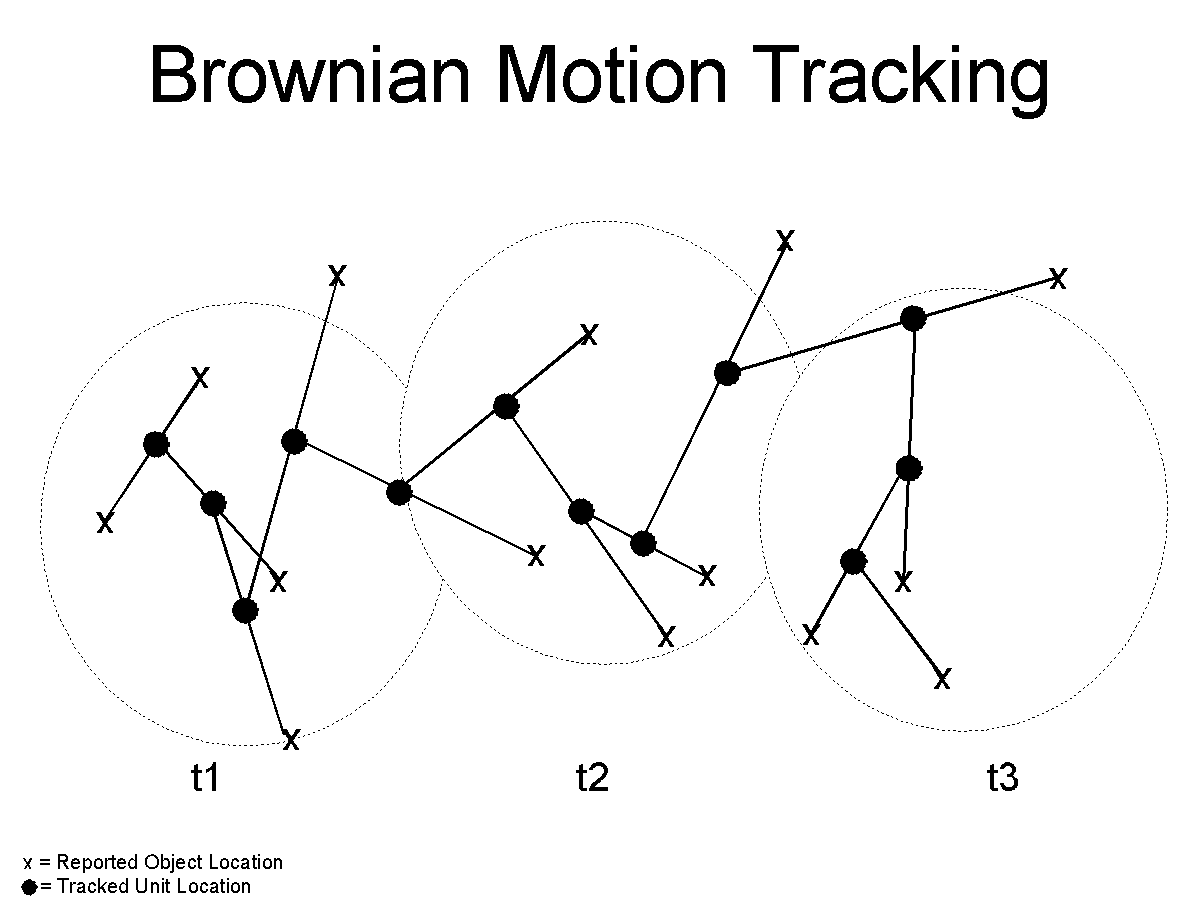
Figure 5. TALON Location Tracking Technique
In order to service the operational community and provide targets for indirect-fire weapons, TALON has been designed to track the most densely populated area as the location of the enemy unit. This is done with a technique we have named "Brownian Motion Tracking". Since each object "floats" around the battlefield unconnected to any other object, but dependent upon all of the objects in the unit, we are detecting "free floating" particles which are being directed enmass by the flow of the unit as a whole, the "medium". The method of location tracking is shown in figure 5. Each object detected is used as an attractor to pull the reported unit location toward itself. Each object is assigned an equal attractive weight. Since the unit is moving as time progresses, all detections must be ordered by time. This provides greater control to later detections and diminishing control to past locations. When object A becomes the first object detected, the unit is assigned location L1, where
Using this method, older detections diminish in importance as new detections are calculated in, giving newer detections the dominating strength. This characteristic enforces the tenancy for the unit location to move toward the center-of-mass of the unit and to follow the unit across the battlefield as it moves. But, it has the disadvantage that objects far off on the perimeter have a serious short-term effect on the assigned location of the unit. It is possible for all of the good information about a unit to be temporarily thrown far to one side by the detection of peripheral objects. This negative effect is balanced by the fact there are more objects influencing the center-of-mass location than the periphery.
Identity. The identity of the unit can vary through four distinct stages:
The lowest of these levels is the default used when something has been located but no further information can be discovered. Size can be determined using information from any of the intelligence disciplines. IMINT can detect enough vehicles in an area to determine the minimum size of the unit, and bounding the area can imply a maximum size. Once TALON has collected a certain percentage of the equipment in a unit, it is allowed to report the size of that unit.
The type of the unit can be added only when specific characteristics have been collected which indicate this. Earlier descriptions of the ELINT and COMINT analysis show how this is done.
The actual name of the unit can only be provided by COMINT. The use of radios in specific ways form a pattern which may be as clear as a fingerprint in identifying the transmitter. Complete historical databases allow both real analysts and TALON to discover the unit identity from this information. Neither ELINT nor IMINT has the power to produce this level of identification.
Activity. A unit's activity refers to the type of operation being undertaken and the formation of the objects in the unit while performing this task. When IMINT is able to image a significant percentage of the objects belonging to a unit it may be possible to determine the formation and hence the activity of the unit. The most recognizable of these formations are a convoy moving down a road and a unit attempting to make a river crossing. In these cases the number of objects required for identification is low, while it is high for units in defense and attack.
ELINT is less useful in determining activity. The change from peace-time mode to war-time mode is very distinct, but the information we are interested in involves changes in unit activity once the battle has commenced. Since this is difficult to determine it is not likely that ELINT will make contributions to activity determination.
Since COMINT is much more descriptive, it can be used to determine unit activity. Parameters are set which give the probability of determining activity based on COMINT signal collection. This probability is determined by empirical data provided by the human analysts.
Data Degradation
Ideally, TALON will have access to IMINT for exact locations and some activities, ELINT for timely locations and unit type, and COMINT for unit identification, timely locations, and activity indicators. Any two of the three are sufficient for analysis and reporting, but a single form can rarely provide enough clues to allow the fusion process to be carried out.
Conspiring against this analysis is the changing nature of the battlefield and the time delays in collecting and reporting information. Though a unit may be well identified at one point in time, if intelligence does not continue to arrive on the unit, the existing data will begin to decay in value. Therefore, the master list will be downgraded, losing information that had previously been timely and dependable for military planning and targeting.
Intelligence may also be lost during times of intense collection. TALON mimics the limitations of the humans assigned to an intelligence cell. Traffic flow may be so high that reports are not worked on until well after time sensitive information has degraded to uselessness. In these cases, TALON will ignore or delete the information just as human analysts would. Since TALON is a computer working on data records, a governor on its performance is essential for limiting it to capacities matching its human counterparts.
BLACKBOARD MAINTENANCE
The master list is shared with the report writer via a blackboard or shared memory mechanism. The report writer is responsible for determining what of the analyzed data should be placed in the delivered report. This is controlled by parameters provided by the trainees and by protocols generally used within the MI community.
The report writer has two primary duties, the first is to schedule the creation of the next SITREP and statistics report. These are generated on a timed basis according to the desires of the trainees. The second is to monitor the blackboard for any information that has been designated as a high priority target (HPT). When these are found it must create a SALUTE report for immediate delivery to the training audience. All reports are dependent upon changes being made to the blackboard by the fusion engine. All blackboard records modified by the fusion engine are flagged to notify the report writer that the information needs to be sent out in the next report.
There are other criteria for including data in a report. Since the trainees may represent many different levels of the command structure and have different interests, they are able to set filters on the data they receive. The first of these is the time interval and, the second is the list of HPTs described above. They may also set a "minimum echelon of interest" which defines the size an enemy unit must be to be included in the report. Large units, like divisions, have little or no interest in the activities of individual enemy companies. Therefore, they may set their minimum echelon of interest at battalions, eliminating data on companies, platoons, and squads that are operating on the battlefield. Should TALON detect these, they will not be added to the report unless they are determined to be part of a larger unit, a determination known as a "roll-up". Intelligence analysts often receive data about small units which, alone, is not of interest to their command structure. But when several reports are integrated together they may indicate the presence and activity of larger units. This is a second layer of correlation embedded within the fusion process, but vertical correlation rather than the earlier horizontal.
The information in a SITREP (figure 4) describes all of the units being actively tracked. The records are written to the report in the order of the certainty of the information being reported. In some cases, dividers are added within the report to indicate where the certainty crosses the 33% and 67% boundaries. A minimum level of certainty filter can be used to exclude reports which are not deemed to be reliable enough to be passed to the intelligence officers in the G2.
A final filter which is nearly an MI standard is the exclusion of units from HPT reports (SALUTEs) which include the term "Unidentified". Information of this type is so vague that it is almost impossible to consider it high priority.
The report writer can provide one more piece of data in the reports. This is a set of points on the battlefield which define the forward edge of the enemy forces opposing the trainees. Known as the FEBA, it is a dividing line between friendly and enemy controlled terrain. This is not mandatory and can be excluded should the trainees need to exercise their own skills in determining this line.
SYSTEM FIELDING AND OPERATIONS
TALON is currently fielded at the TACSIM sites at U.S. Forces Korea; V Corps, Germany; I Corps, Washington; III Corps, Texas; TEXCOM, Texas; National Simulation Center, Kansas; Intelligence Center and School, Arizona; and the TACSIM Project Office, Virginia. It is used in dozens of exercises each year and has been shown to produce results comparable to that of human analysis cells. This is not to imply that it is a near perfect representation of the process. Rather, given the huge numbers of reports analyzed (tens of thousands), the results are sufficient for providing useful input to the operational planning process. If individual TALON decisions were to be compared with equivalent decisions from humans we believe there would be noticable variations. But, over large volumes and long time periods, the two processes tend to achieve similar levels of information.
The system has been used for missions beyond its original design. As a fusion engine it can reduce the amount of message traffic being placed on a network. In cases where the communications capabilities are limited this can make a valuable contribution to the ability of certain customers to join the exercise. The HPT report writer has been used as an alarm process for the exercise controllers. When key data is received, a SALUTE message is generated and transmited directly to exercise controllers. These are then in a position to prepare for and observe the reaction of the trainees upon receiving this key data. This enhances the ability of the controllers to use exercises as evaluation tools on training audiences.
Since TALON replicates the performance of a cell of human analysts, both could be fed the same sets of data. They could then be compared to each other to identify the differences. Initially this would calibrate TALON to make it a more accurate representation of the best human cell available. Once TALON is calibrated the same process could be used to evaluate the analysis capabilities of the humans in other cells being trained. We describe this as "could" since it has not been done at the time of this writing.
TALON has been used to aid in the development of several intelligence processing systems. It can feed correctly formatted data to systems still in the development mode. This eliminates the need for a real-world operation (e.g. Desert Storm) to stress the system, or a huge man-power effort to replicate these situations. This type of stimulation of the All Source Analysis System (ASAS) is the primary mission of the TACSIM site located at TEXCOM, Fort Hood, Texas. Preliminary efforts are underway to use TALON to aid in the development of the Single Intelligence Correlator (SICOR) and the Multiple Intelligence Correlator (MICOR). These are systems which perform the same functions in the real-world that TALON does in simualtion. Once developed, tested, and fielded, these may have a significant impact on the utility of TALON in the future.
CONCLUSION
This paper has described the operations of the TACSIM Analysis Operations Node (TALON), particularly the intelligence fusion engine and report writers resident therein. The analysis/fusion performed by the system is controlled by value-based algorithms derived from extensive interviews and design meetings with human intelligence analysts. The degree of success of the system is closely related to the huge magnitude of messages that must be analyzed during an exercise. Over large numbers of reports and significant time durations the results produced by TALON follow the same trends as the results produced by a cell of human analysts.
Aware of current limitations and the difficulty in tracing decisions through the system, the STRICOM TACSIM Project Office, has investigated the possibility of improving the algorithms resident within TALON. The goal is to create a system which can be compared to human performance on an individual decision level, and whose analytical steps can be described clearly to ranking military officers. This proposal involves the use of an expert system to store and retrieve the knowledge and techniques communicated to the system developers by intelligence analysts. The fusion process also seems to lend itself well to the application of neural networks. The TACSIM Project Office has opened communications with neural network researchers at Colorado University in order to explore this technology.
The expert system and neural network will be used to identify trends in intelligence reports and find relationships that have been obscured by the splintered nature of the reports and their dispersion through time. If these exist, and can be identified we hope to eliminate our dependance upon ground truth information to correlate reports. This may allow us to develop a true fusion system from the seeds of a simulation system. Current system design methods rely upon known relationships in order to develop a working system. We hope to explore the possibility of simulation-based design, in which validated simulations can be used to replicate a systems capabilities, and from there can evolve into a real system free of the constraints and special environemnts of a simulation. This technique may lead to system designs and algorithms which may not have been explored through traditional design techniques. It may also illustrate that a system capability can be created which performs its tasks correctly, but whose mechanisms are not completely understood. This is similar to the early uses of electricity, where tools could be built based upon experimental results, but where no understanding of the physics was yet available.
BIBLIOGRAPHY
Corps Battle Simulation: Analyst's Guide - Air/Ground/Logistics (3 Volumes), Jet Propulsion Laboratory, Pasadena, California, 1993.
The DIS Vision: A Map to the Future of Distributed Simulation, Institute for Simulation and Training, Orlando, Florida, January, 1993.
DMSO Survey of Semi-Automated Forces, Defense Modeling and Simulation Office, March 15, 1993.
Fishwick, Paul A., Simulation Model Design and Execution: Building Digital Worlds, Prentice Hall, Englewood Cliffs, NJ, 1995.
Hall, David L., Mathematical Techniques in Multisensor Data Fusion, Artech House, Boston, MA, 1992.
Hofstadter, Douglas, Fluid Concepts and Creative Analogies: Computer Models of the Fundamental Mechanisms of Thought, Basic Books, New York, NY, 1995.
Hogg, Robert V. and Tanis, Elliot A., Probability and Statistical Inference, Macmillan Publishing, New York, NY, 1977.
Kerchner, Robert M., "Scaling Problems Associated with Rule-Based Decision Algorithms in Multiple-Objective Situations -- Value-Driven Methods as an Alternative", Proceedings of the 1995 Electronic Conference on Scalability in Training Simulation, June, 1995.
Knepell, Peter L. and Arangno, Deborah C., Simulation Validation: A Confidence Assessment Methodology, IEEE Computer Society Press, Los Alamitos, CA, 1993.
Kolodner, Janet, Case-Based Reasoning, Morgan Kaufmann Publishers, San Mateo, CA, 1993.
Smith, Roger D., editor, Proceedings of the 1994 Electronic Conference on Constructive Training Simulation, World Wide Web Event, April, 1994.
TACSIM Analysis Operations Node: User's Manual, TACSIM Project Office, Unpublished Document, 1992.
TACSIM Operations Manual Volume I: Simulator Operations, United States Army Test and Experimen- tation Command, Unpublished Document, 1989.
Zeigler, Bernard P., Object-Oriented Simulation with Hierarchical, Modular Models: Intelligent Agents and Endomorphic Systems, Academic Press, Boston, MA, 1990.
ABOUT THE AUTHOR
Roger D. Smith is Principal Simulation Engineer for Mystech Associates. He is responsible for developing simulations and tools to support the training missions of US and Allied forces around the world. These have included air and ground combat models, intelligence collection and analysis algorithms, after action review systems, and simulation management tools. He is currently interested in the integration of constructive and virtual simulations and the use of embedded simulations in operational military systems.